The Mobile Device Management (MDM) protocol provides a way for system administrators to send device management commands to managed iOS devices running iOS 4 and later, macOS devices running macOS v10.7 and later, and Apple TV devices running iOS 7 (Apple TV software 6.0) and later. MDM allows for OS level control of multiple devices from a centralized location. A remote administrator can install/remove apps, install/revoke certificates, lock the device, change password requirements, etc. You can read more about Mobile Device Management here.
Warning - If you are planning to implement MDM protocol for your production application which you want to distribute via AppStore then I'm sorry to tell you, you can't do this. Because since November 2018, using MDM/VPN for ad blocking or screen-time monitoring is not considered compliant with the App Store Review Guidelines. Read more about this here.
Update (28 Apr 2019) - Apple release press update about the Parental Control Apps.
Update (09 July 2019) - Apple restores banned from apps which are using MDM to the App Store.
1. Create MDM Vendor CSR
- Open Keychain Access.
- Go to the menu bar: Keychain Access -> Certificate Assistant -> Request a Certificate From a Certificate Authority.
- Use the same email as the developer account that will be used. Enter in a common name as well.
- Select Saved to disk.

Note - Save all file in same directory (let's say MDM).
2. Upload CSR to Apple
- Go to Apple's Certificates, Identifiers & Profiles page.
- Select MDM CSR under Production. If this option is disabled, you will need to contact apple to enable it. You can either email apple at devprograms@apple.com or go through the online contact menu. In your message, indicate that you are looking to create an MDM Vendor Certificate and need the MDM CSR option enabled on the certificate creation page. Apple should respond within one business day according to their contact page.

- When you have the MDM CSR option available, select it and hit continue. Hit continue again through Apple's description of how to create a CSR file (we already have one).

- Upload the .certSigningRequest file we created in step 1 and then hit generate.
- A .cer file should be downloaded. Name it something like
mdmvendor.cer. - You can also download .cer file later from Certificates section.

3. Export MDM private key
- Open your
mdmvendor.cerfile in Keychain Access. - Select Certificates from the left side.
- You should find your certificate listed as MDM Vendor: Common Name.
- There should be an arrow on that line that opens up show the MDM private key.
- Right-click the private key, select Export..., and save as
private.p12

- Remember where you save this file, we will use it in step 5.
4. Create Push Certificate CSR
- In Keychain Access, again select from the menu bar: Keychain Access -> Certificate Assistant -> Request a Certificate From a Certificate Authority.
- Enter your email (can be a different email) and a common name.
- Select Saved to disk and name it
push.csr. (Same as Step 1)

5. Extract MDM private key and MDM Vendor Certificate
Open terminal and change the directory to the MDM directory, which you created in Step 1. Also, make sure at this stage MDM directory must contains following 4 files -

-
Extract private key using the following command:
If you've added any password inprivate.p12file during export in step 3 you need to enter same import password in this command. Also you need to enter PEM pass phrase. This pass phrase will be requires in next command.openssl pkcs12 -in private.p12 -nocerts -out key.pem -
Strip the password from the private key using the following command:
This command ask you to enter pass phrase forkey.pem, here you need to enter same pass phrase which you entered in last command.openssl rsa -in key.pem -out private.key -
Extract certificate using the following command:
Again, if you've added any password inprivate.p12file during export in step 3 you need to enter same import password in this command.openssl pkcs12 -in private.p12 -clcerts -nokeys -out cert.pem -
Convert certificate to DES using the following command:
openssl x509 -in cert.pem -inform PEM -out mdm.cer -outform DES -
In this step you've created 4 files
key.pem,private.key,cert.pemandmdm.cer. These files will be used in the next step. After this step you MDM directory will look like this -

6. Use the mdmvendorsign tool to create applepush.csr
-
We're going to use the python code located in
/vendor/of the repository. So, you need to clone this repository. To clone, run this commandgit clone https://github.com/vineetchoudhary/Apple-iOS-MDM-Server.git -
Now, copy
private.key,push.csr, andmdm.cerintoApple-iOS-MDM-Server/vendor/. You can run these command to copy -cp push.csr ./Apple-iOS-MDM-Server/vendor/ cp private.key ./Apple-iOS-MDM-Server/vendor cp mdm.cer ./Apple-iOS-MDM-Server/vendor/ # Change directory cd Apple-iOS-MDM-Server/vendor/ -
Run the following command while in that directory:
python mdm_vendor_sign.py --key private.key --csr push.csr --mdm mdm.cer --out applepush.csrThis should generate
applepush.csr.
7. Get Push Certificate from Apple
- Go to Apple's Push Certificates Portal and click the Create a Certificate button.

- Upload
applepush.csrto create a new entry in the table. - Download the resulting push certificate.

- Open the push certificate in Keychain Access.
8. Prepare Push Certificate
- Find the push certificate in Keychain Access. It should look like
APSP:hexstuffhere. - Right-click the certificate and select Get Info.
- Copy down the User ID which should look like
com.apple.mgmt.External.hexstuffhere.... We will use it later

- Right-click the certificate and select Export... and save it as
mdm.p12

- Run the following command to convert it to a pem file. Again, if you've added any password in
mdm.p12file during export you need to enter same import password in this command.openssl pkcs12 -in mdm.p12 -out PushCert.pem -nodes - Copy the resulting
PushCert.pemfile to/server/. You can use this command to copy -cp PushCert.pem ./Apple-iOS-MDM-Server/scripts/
9. Generate additional certs
- Go to the
scriptsdirectory and rename the different part of your domain SSL certificate as following -- Rename your Certificate Authority (CA) certificate to
cacert.crt,identity.crtandserver.crt(Same file with three different names). Your CA cetificate content looks like this ------BEGIN CERTIFICATE----- MIIFPDCCBCSgAwIBAgIJALJxXxDRdGWNMA0GCSqGSIb3DQEBCwUAMIG0MQswCQYD VQQGEwJVUzEQMA4GA1UECBMHQXJpem9uYTETMBEGA1UEBxMKU2NvdHRzZGFsZTEa MBgGA1UEChMRR29EYWRkeS5jb20sIE................................. .............................pyoNqhOasNUfoAbPgmXt+zXiy9AZWOds6Dc PtRTSsEEfATviu+nd7jrjS6AW/g4UKBorujxHYtGoqVfNx6aCqHMS+gmH0JbSnX9 -----END CERTIFICATE----- - Rename your server Certificate Signing Request (CSR) file to
identity.csr. The content of CSR file looks like this ------BEGIN CERTIFICATE REQUEST----- MIIDAzCCAesCAQAwgaIxCzAJBgNVBAYTAkFVMRgwFgYDVQQIDA9Tb3V0aCBBdXN0 cmFsaWExETAPBgNVBAcMC........................................... ...........................mqeUCKtYnoCE/zkUUPErkHq4dWo3f+JGPC4Dt Onj3dUOtkKJifHw0iknYl+fIMnoYfRsVKQ9d3GVKGqb/A4s4qFzbQWbU1rNq9Sx9 mZgrKORxjA== -----END CERTIFICATE REQUEST----- - Rename your server SSL certificate private key to
cakey.key,server.keyandidentity.key(Same file with three different names). The content of CSR file looks like this ------BEGIN PRIVATE KEY----- MIIEvQIBADANBgkqhkiG9w0BAQEFAASCBKcwggSjAgEAAoIBAQD2Xh1z9I4rWZ9J t5EyoJtH2ImS7UQo5bABItKkYFjP50towTD4+k2PfgPZCRJ3kDSlOVSLHzfD57qB kCv/UG29nbbIkFH6aqjhfaj......................................... .................................j8yc3sduzKMd+KoZGGLzEhB/JEFTrHn jWwvMQENHRawj/Jocsc0PUA= -----END PRIVATE KEY-----
- Rename your Certificate Authority (CA) certificate to
- Now, run
make_certs.sh. You need to create an export password. You'll need to include it in the MDM profile.

- This will generate a number of necessary certificates to move forward.
- All certificates will be automatically moved to their proper location in
/server. We'll useidentity.p12in step 10 to create anEnroll.mobileconfigfile.
10. Create Enroll.mobileconfig
- Open the Apple Configurator 2, click File option in menu bar, and then click the New Profile.
- In the General category, pick a name to identify the cert. For Identifier, use the
com.apple.mgmt.External.hexstuffherethat you copied down in step 8.
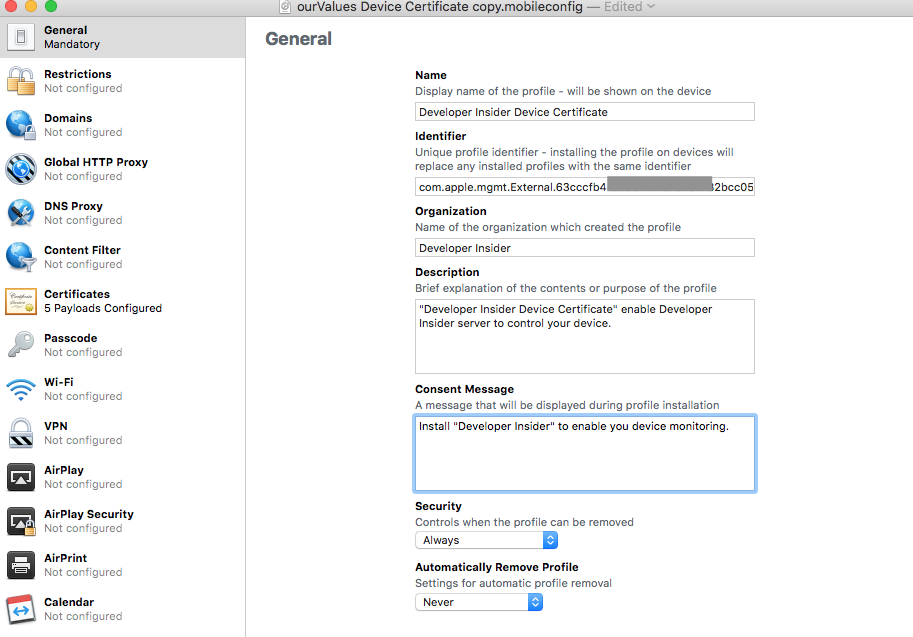
- In the Certificates category, click configure and find your
scripts/identity.p12file generated in step 9. For password, we either use the PEM password or the export password. Also, add theserver.crt,Apple Root CA,Apple Worldwide Developer Relations CA - G2andApple Worldwide Developer Relations Certification Authoritycertificates. You can download these certificates from Apple website. So, here you need to add total 5 certificates.

- Now, save this mobile configuration as
Enroll.mobileconfig.
11. Config Mobile Device Management
-
For Mobile Device Management, Open
Enroll.mobileconfigfile in any text editor. YourEnroll.mobileconfigfile looks like this -<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>ConsentText</key> <dict> <key>default</key> <string>Install "Developer Insider" to enable you device monitoring.</string> </dict> <key>PayloadContent</key> <array> <dict> <key>PayloadCertificateFileName</key> <string>server.crt</string> <key>PayloadContent</key> <data> LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUZQRENDQkNT Z0F3SUJBZ0lKQUxKeFh4R............................... .....................ElNNUN1ZgpSZVlObnlpY3Nia3FXbGV0 TncrdkhYL2J2Wjg9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>*.example.com</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.4AA9D1AB-XXXX-XXXX-XXX-1E9280222697</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>4AA9D1AB-XXXX-XXXX-XXXX-1E9280222697</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleIncRootCertificate.cer</string> <key>PayloadContent</key> <data> MIIEuzCCA6OgAwIBAgIBAjANBgkqhkiG9w0BAQUFADBiMQswCQYD VQQGEwJVUzETMBEGA1U................................. ................xw8dtk2cXmPIS4AXUKqK1drk/NAJBzewdXUh </data> <key>PayloadDescription</key> <string>Adds a CA root certificate</string> <key>PayloadDisplayName</key> <string>Apple Root CA</string> <key>PayloadIdentifier</key> <string>com.apple.security.root.57B909F1-XXXX-XXXX-XXXX-B066B59CA281</string> <key>PayloadType</key> <string>com.apple.security.root</string> <key>PayloadUUID</key> <string>57B909F1-XXXX-XXXX-XXXX-B066B59CA281</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleWWDRCAG2.cer</string> <key>PayloadContent</key> <data> MIIC9zCCAnygAwIBAgIIb+/Y9emjp+4wCgYIKoZIzj0EAwIwZzEb MBkGA1UEAwwSQXBwbGUgUm9v............................ ....................FUOixRLal1BzfF7QbrJcYlDXUfE6Wg== </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>Apple Worldwide Developer Relations CA - G2</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.685F84A4-XXXX-XXXX-XXXX-4EBD1021F707</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>685F84A4-XXXX-XXXX-XXXX-4EBD1021F707</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleWWDRCA.cer</string> <key>PayloadContent</key> <data> MIIEIjCCAwqgAwIBAgIIAd68xDltoBAwDQYJKoZIhvcNAQEFBQAw YjELMAkGA1UEBhMCVVMxEzA............................. ................05Cdqa3zr/04GpZnMBxRpVzscYqCtGwPDBUf </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>Apple Worldwide Developer Relations Certification Authority</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.1BD58990-XXXX-XXXX-XXXX-7D09252A9190</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>1BD58990-XXXX-XXXX-XXXX-7D09252A9190</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>Password</key> <string>test@123</string> <key>PayloadCertificateFileName</key> <string>identity.p12</string> <key>PayloadContent</key> <data> MIIeyQIBAzCCHo8GCSqGSIb3DQEHAaCCHoAEgh58MIIeeDCCGS8G CSqGSIb3DQEHBqCCGSAwghk............................. ....................DAyJB5BmDPMECJpm+FuDUe5tAgIIAA== </data> <key>PayloadDescription</key> <string>Adds a PKCS#12-formatted certificate</string> <key>PayloadDisplayName</key> <string>identity.p12</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs12.38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadType</key> <string>com.apple.security.pkcs12</string> <key>PayloadUUID</key> <string>38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </array> <key>PayloadDescription</key> <string>"Developer Insider Device Certificate" enable Developer Insider server to control your device.</string> <key>PayloadDisplayName</key> <string>Developer Insider Device Certificate</string> <key>PayloadIdentifier</key> <string>com.apple.mgmt.External.63cccfb4-XXXX-XXXX-XXXX-82bcc05a2535</string> <key>PayloadOrganization</key> <string>Developer Insider</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>0CF6836A-XXXX-XXXX-XXXX-12B61C878FB4</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist> -
Now we need to add following MDM options dictionary into
PayloadContentarray ofEnroll.mobileconfig.<dict> <key>AccessRights</key> <integer>4096</integer> <key>CheckInURL</key> <string>https://YOUR_HOSTNAME_OR_IP:8080/checkin</string> <key>CheckOutWhenRemoved</key> <true/> <key>IdentityCertificateUUID</key> <string>38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadDescription</key> <string>Configures MobileDeviceManagement.</string> <key>PayloadIdentifier</key> <string>com.apple.mdm.34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E</string> <key>PayloadOrganization</key> <string>Developer Insider</string> <key>PayloadType</key> <string>com.apple.mdm</string> <key>PayloadUUID</key> <string>34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E</string> <key>PayloadVersion</key> <integer>1</integer> <key>ServerURL</key> <string>https://YOUR_HOSTNAME_OR_IP:8080/server</string> <key>SignMessage</key> <true/> <key>Topic</key> <string>com.apple.mgmt.External.63cccfb4-XXXX-XXXX-XXXX-82bcc05a2535</string> <key>UseDevelopmentAPNS</key> <false/> </dict> -
Structure of MDM Payloads
The Mobile Device Management (MDM) payload, a simple property list, is designated by thecom.apple.mdmvalue in thePayloadTypefield. This payload defines the following keys specific to MDM payloads:Key Type Description IdentityCertificateUUID String Mandatory. UUID of the certificate payload for the device’s identity. It may also point to a SCEP payload. You need to use the `PayloadUUID` of the `identity.p12` in this field.
IdentityCertificateUUID String Mandatory. Here you need to generate a UUID. You can use `uuidgen` to generate an UUID and then copy paste that UUID in this field. UUID looks like this 34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E
PayloadIdentifier String Here you need to append the UUID in after `com.apple.mdm.` which we generated in last step. Your payload identifier looks like this com.apple.mdm.34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E Topic String Mandatory. The topic that MDM listens to for push notifications. The certificate that the server uses to send push notifications must have the same topic in its subject. The topic must begin with the
com.apple.mgmt.External.hexstuffhere...prefix.ServerURL String Mandatory. The URL that the device contacts to retrieve device management instructions. Must begin with the
https://URL scheme, and may contain a port number (https://YOUR_HOSTNAME_OR_IP:PORT/server, for example).CheckInURL String Optional. The URL that the device should use to check in during installation. Must begin with the
https://URL scheme and may contain a port number (https://YOUR_HOSTNAME_OR_IP:8080/checkin, for example). If this URL is not given, theServerURLis used for both purposes.CheckOutWhenRemoved Boolean Optional. If
true, the device attempts to send aCheckOutmessage to the check-in server when the profile is removed. Defaults tofalse.AccessRights Integer, flags Required. Logical OR of the following bit-flags:
- 1: Allow inspection of installed configuration profiles.
- 2: Allow installation and removal of configuration profiles.
- 4: Allow device lock and passcode removal.
- 8: Allow device erase.
- 16: Allow query of Device Information (device capacity, serial number).
- 32: Allow query of Network Information (phone/SIM numbers, MAC addresses).
- 64: Allow inspection of installed provisioning profiles.
- 128: Allow installation and removal of provisioning profiles.
- 256: Allow inspection of installed applications.
- 512: Allow restriction-related queries.
- 1024: Allow security-related queries.
- 2048: Allow manipulation of settings.
- 4096: Allow app management.
May not be zero. If 2 is specified, 1 must also be specified. If 128 is specified, 64 must also be specified.
UseDevelopmentAPNS Boolean Optional. If
true, the device uses the development APNS servers. Otherwise, the device uses the production servers. Defaults tofalse. Note that this property must be set to false if your Apple Push Notification Service certificate was issued by the Apple Push Certificate Portal. That portal only issues certificates for the production push environment. -
Now save the file as
Enroll.mobileconfigand move it to the/serverdirectory. -
Your final
Enroll.movbileconfigwill be looks like this -<?xml version="1.0" encoding="UTF-8"?> <!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd"> <plist version="1.0"> <dict> <key>ConsentText</key> <dict> <key>default</key> <string>Install "Developer Insider" to enable you device monitoring.</string> </dict> <key>PayloadContent</key> <array> <dict> <key>PayloadCertificateFileName</key> <string>server.crt</string> <key>PayloadContent</key> <data> LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCk1JSUZQRENDQkNT Z0F3SUJBZ0lKQUxKeFh4R............................... .....................ElNNUN1ZgpSZVlObnlpY3Nia3FXbGV0 TncrdkhYL2J2Wjg9Ci0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0K </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>*.example.com</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.4AA9D1AB-XXXX-XXXX-XXX-1E9280222697</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>4AA9D1AB-XXXX-XXXX-XXXX-1E9280222697</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleIncRootCertificate.cer</string> <key>PayloadContent</key> <data> MIIEuzCCA6OgAwIBAgIBAjANBgkqhkiG9w0BAQUFADBiMQswCQYD VQQGEwJVUzETMBEGA1U................................. ................xw8dtk2cXmPIS4AXUKqK1drk/NAJBzewdXUh </data> <key>PayloadDescription</key> <string>Adds a CA root certificate</string> <key>PayloadDisplayName</key> <string>Apple Root CA</string> <key>PayloadIdentifier</key> <string>com.apple.security.root.57B909F1-XXXX-XXXX-XXXX-B066B59CA281</string> <key>PayloadType</key> <string>com.apple.security.root</string> <key>PayloadUUID</key> <string>57B909F1-XXXX-XXXX-XXXX-B066B59CA281</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleWWDRCAG2.cer</string> <key>PayloadContent</key> <data> MIIC9zCCAnygAwIBAgIIb+/Y9emjp+4wCgYIKoZIzj0EAwIwZzEb MBkGA1UEAwwSQXBwbGUgUm9v............................ ....................FUOixRLal1BzfF7QbrJcYlDXUfE6Wg== </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>Apple Worldwide Developer Relations CA - G2</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.685F84A4-XXXX-XXXX-XXXX-4EBD1021F707</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>685F84A4-XXXX-XXXX-XXXX-4EBD1021F707</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>PayloadCertificateFileName</key> <string>AppleWWDRCA.cer</string> <key>PayloadContent</key> <data> MIIEIjCCAwqgAwIBAgIIAd68xDltoBAwDQYJKoZIhvcNAQEFBQAw YjELMAkGA1UEBhMCVVMxEzA............................. ................05Cdqa3zr/04GpZnMBxRpVzscYqCtGwPDBUf </data> <key>PayloadDescription</key> <string>Adds a PKCS#1-formatted certificate</string> <key>PayloadDisplayName</key> <string>Apple Worldwide Developer Relations Certification Authority</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs1.1BD58990-XXXX-XXXX-XXXX-7D09252A9190</string> <key>PayloadType</key> <string>com.apple.security.pkcs1</string> <key>PayloadUUID</key> <string>1BD58990-XXXX-XXXX-XXXX-7D09252A9190</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <dict> <key>Password</key> <string>test@123</string> <key>PayloadCertificateFileName</key> <string>identity.p12</string> <key>PayloadContent</key> <data> MIIeyQIBAzCCHo8GCSqGSIb3DQEHAaCCHoAEgh58MIIeeDCCGS8G CSqGSIb3DQEHBqCCGSAwghk............................. ....................DAyJB5BmDPMECJpm+FuDUe5tAgIIAA== </data> <key>PayloadDescription</key> <string>Adds a PKCS#12-formatted certificate</string> <key>PayloadDisplayName</key> <string>identity.p12</string> <key>PayloadIdentifier</key> <string>com.apple.security.pkcs12.38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadType</key> <string>com.apple.security.pkcs12</string> <key>PayloadUUID</key> <string>38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadVersion</key> <integer>1</integer> </dict> <key>AccessRights</key> <integer>4096</integer> <key>CheckInURL</key> <string>https://YOUR_HOSTNAME_OR_IP:8080/checkin/</string> <key>CheckOutWhenRemoved</key> <true/> <key>IdentityCertificateUUID</key> <string>38236F74-XXXX-XXXX-XXXX-5C4923A303FA</string> <key>PayloadDescription</key> <string>Configures MobileDeviceManagement.</string> <key>PayloadIdentifier</key> <string>com.apple.mdm.34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E</string> <key>PayloadOrganization</key> <string>Developer Insider</string> <key>PayloadType</key> <string>com.apple.mdm</string> <key>PayloadUUID</key> <string>34995C2E-XXXX-XXXX-XXXX-D6DB637A1D6E</string> <key>PayloadVersion</key> <integer>1</integer> <key>ServerURL</key> <string>https://YOUR_HOSTNAME_OR_IP:8080/server/</string> <key>SignMessage</key> <true/> <key>Topic</key> <string>com.apple.mgmt.External.63cccfb4-XXXX-XXXX-XXXX-82bcc05a2535</string> <key>UseDevelopmentAPNS</key> <false/> </dict> </array> <key>PayloadDescription</key> <string>"Developer Insider Device Certificate" enable Developer Insider server to control your device.</string> <key>PayloadDisplayName</key> <string>Developer Insider Device Certificate</string> <key>PayloadIdentifier</key> <string>com.apple.mgmt.External.63cccfb4-XXXX-XXXX-XXXX-82bcc05a2535</string> <key>PayloadOrganization</key> <string>Developer Insider</string> <key>PayloadRemovalDisallowed</key> <false/> <key>PayloadType</key> <string>Configuration</string> <key>PayloadUUID</key> <string>0CF6836A-XXXX-XXXX-XXXX-12B61C878FB4</string> <key>PayloadVersion</key> <integer>1</integer> </dict> </plist>
12. Signing / Verify Enroll.mobileconfig Profile
If you try to use current Enroll.mobileconfig using Apple Configurator 2, you've probably noticed that it says ‘Unsigned’ when you send the .mobileconfig file to your device.

In order to sign Enroll.mobileconfi you need to save you server (domain SSL) certificate chain in the server directory with name serverchain.pem. server.crt and server.pem these two files you've already copy in step 9. Now run this command in server directory to generate Signed mobile config profile with name EnrollSigned.mobileconfig.
openssl smime -sign -signer server.crt -inkey server.pem -certfile serverchain.pem -nodetach -outform der -in Enroll.mobileconfig -out EnrollSigned.mobileconfig

13. Cleanup
- Any additional files that are not in
/server/generated during this process are not necessary for running the server. Some of them may have/be private keys or other unique information, so it is probably a good idea to protect or destroy those files. - Most certs will be located in the
/scripts/folder. There may be some certificates are part of your domain SSL certificate, so a good idea is save them elsewhere. - Please secure these files and prevent others from being able to access them.